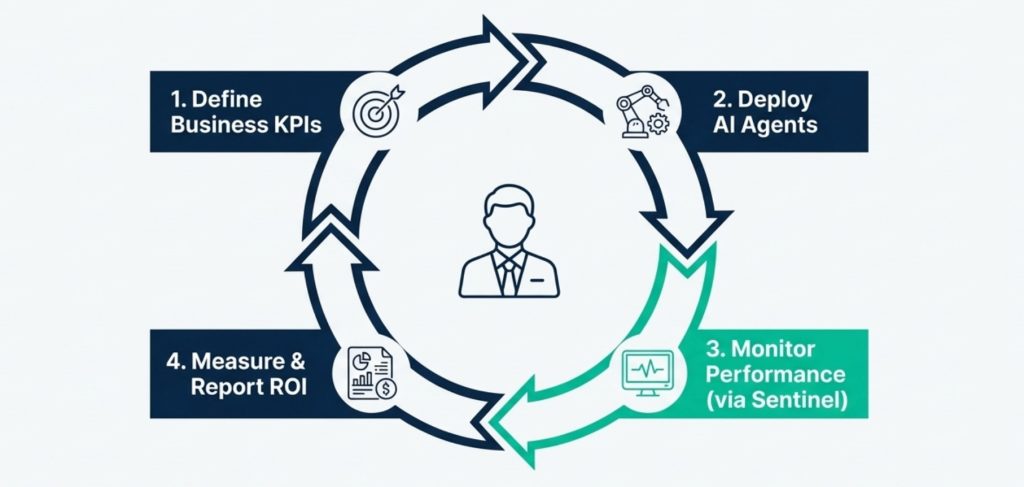
Our Service Methodology: The Intelligence Transformation Cycle
At AIBI-Studio, we do not simply “install AI.” We engineer a transformation. We understand that layering intelligence over a broken process only accelerates chaos. Therefore, our engagement model is a disciplined, multi-stage engineering process designed to modernize legacy workflows, secure sensitive data, and deploy Level 3 Agentic AI that delivers measurable ROI.
Here is how we take your organization from Legacy Process to Intelligent Automation in six strategic phases.
Phase 1:
Phase 2:
Phase 3:
Phase 4:
Phase 5:
Phase 6:
Phase 1: Discovery & The “Chaos Map”
Diagnosing the Reality Before Building the Future.
Before we write a single line of code, we engage in a deep-dive consulting phase to map your current reality. We sit with your stakeholders to understand not just the “SOP” (Standard Operating Procedure), but the actual way work gets done—including the workarounds and hidden inefficiencies.
We focus on extracting the following critical insights:
-
Legacy Process Audits: We trace the full lifecycle of a transaction across your existing systems (ERP, CRM, Spreadsheets) to find bottlenecks.
-
Leakage Identification: We pinpoint exactly where time, money, or data is being lost due to manual hand-offs.
-
Human Error Analysis: We identify high-risk zones where fatigue or lack of training leads to costly mistakes.
-
Proxy Data Detection: We expose areas where your team is using “dummy data” or approximations because the real data isn’t available, ensuring our AI isn’t trained on “garbage.”
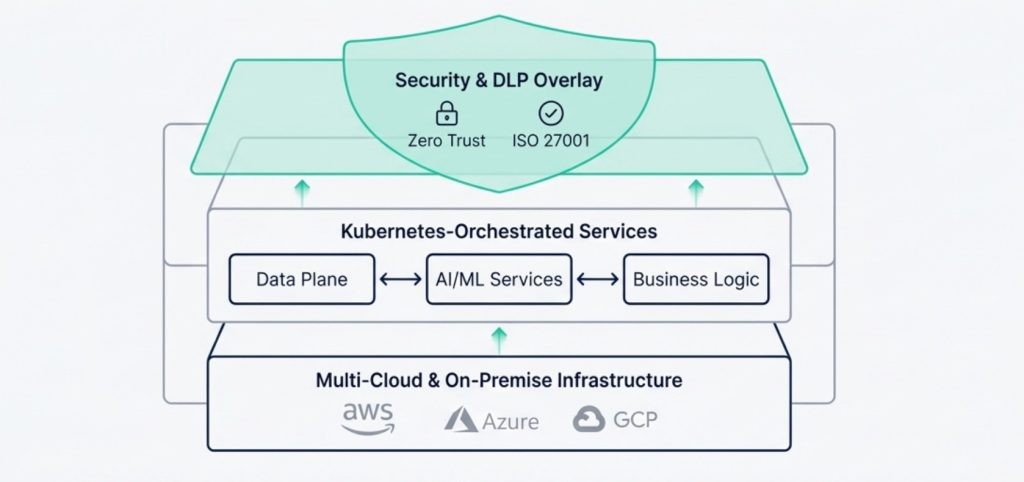
Phase 2: Governance & The Zero-Trust Architecture
Defining the Boundaries of Intelligence.
Once the business goals are aligned, we define the “Rules of Engagement.” Agentic AI is powerful, so it requires strict boundaries. We architect the security layer before the intelligence layer. This ensures that the AI operates autonomously but never goes rogue.
-
Operational Guardrails: We define the strict “Do’s and Don’ts.” For example, an agent may be allowed to draft a refund under $500, but must request approval for anything above.
-
Data Loss Prevention (DLP): We identify all Personal Identifiable Information (PII) and sensitive financial data flowing through the process.
-
The Redaction Engine: We implement our proprietary masking protocols. Names, credit card numbers, and social security numbers are automatically redacted before data enters the reasoning model, ensuring compliance with GDPR, HIPAA, and ISO 27001.
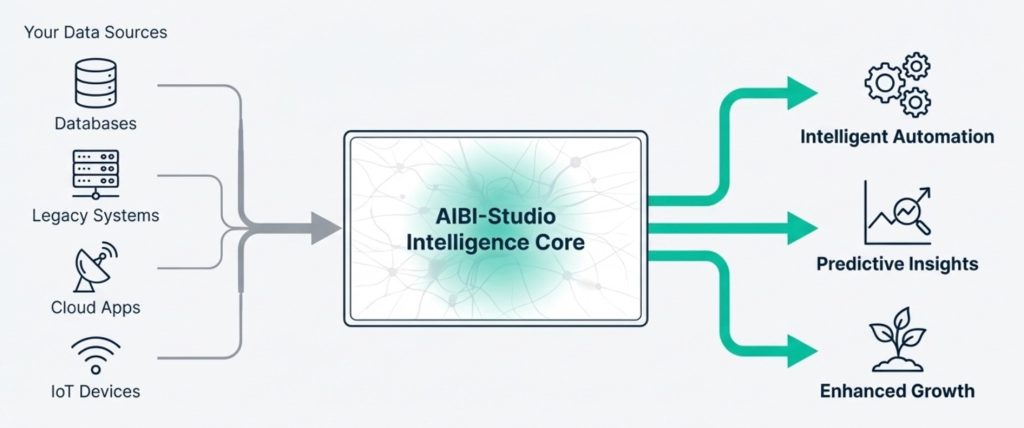
Phase 3: The Connectivity Layer (Adaptors & Triggers)
Bridging the Gap Between Old and New.
We believe in “Keeping the Core, Upgrading the Brain.” We do not rip and replace your legacy systems; we build intelligent bridges to them. In this phase, our engineering team constructs the data pipelines that will fuel the AI agent.
-
Custom Adaptor Creation: We build secure API connectors or direct database links to pull necessary data from your varied sources (SQL Databases, SAP, Salesforce, or even Email inboxes).
-
Event Trigger Mapping: We define what “wakes up” the agent. Is it a new email? A vibration alert from an IoT sensor? A specific time of day?
-
Data Normalization: We convert messy, unstructured data from these sources into a standardized format that the AI can understand and process accurately.
Phase 4: Agent Configuration & Phased Deployment
From Passive Observer to Active Manager.
Now, the “Brain” is activated. However, to mitigate risk, we deploy the Agentic AI in two distinct sub-phases. We do not hand over the keys until the driver has proven they can drive.
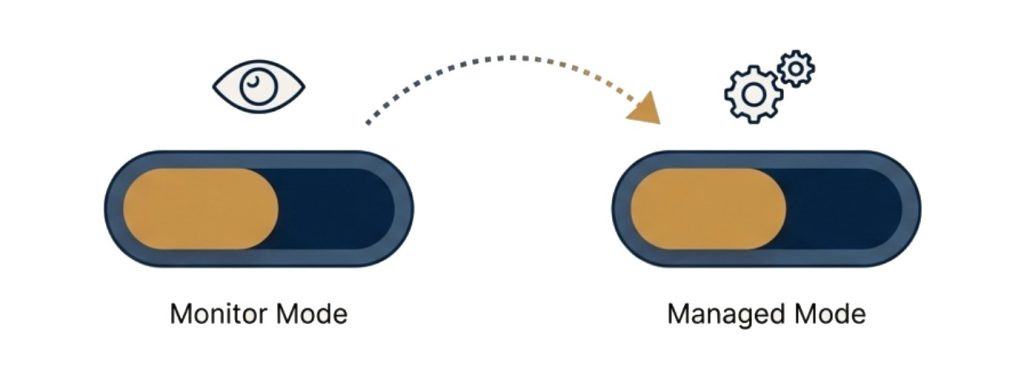
Phase 4A: The “Shadow” (Monitoring Mode)
-
The Agent connects to the live stream of data but takes no action.
-
It monitors the process in real-time, predicting what it would have done versus what the human operator actually did.
-
This generates a “Confidence Score” and highlights any discrepancies in logic.
Phase 4B: The “Co-Pilot” (Active Management)
-
Once the Confidence Score hits the agreed threshold (e.g., 98%), the Agent is granted “Write Access.”
-
The Agent begins actively managing the process—updating the legacy system, sending emails, or dispatching orders—while a human stays in the loop for edge cases.
Phase 5: Rigorous Testing & Recursive Training
Ensuring Perfection Through Stress Testing.
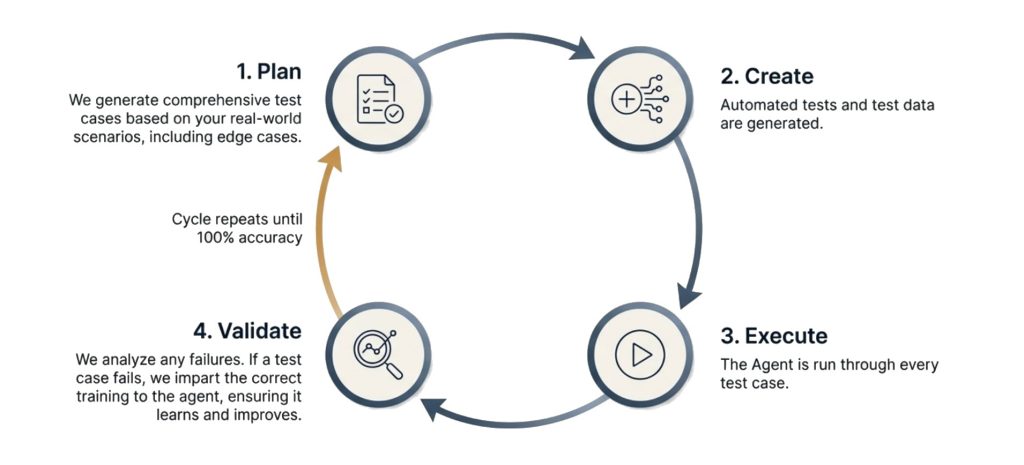
Before full production release, the system enters the “Training Dojo.” We subject the Agent to thousands of potential scenarios, including high-stress edge cases, to ensure resilience.
-
Use Case Validation: We run the Agent against a library of historical scenarios (e.g., “What if the inventory is zero?” or “What if the customer data is incomplete?”).
-
Failure Analysis: If the Agent fails or hallucinates, we don’t just patch the code; we perform Recursive Training. We feed the “correct” behavior back into the model, fine-tuning its decision-making weights.
-
Regression Testing: After retraining, we re-run all previous test cases to ensure the new learning hasn’t broken old logic.
Phase 6: Production & Value Realization
Go-Live and Continuous Optimization.
Once all test cases pass with 100% success rates, the system is promoted to the Production Environment. But our work doesn’t end there.
-
Live Deployment: The Agent takes full ownership of the defined workflow.
-
Sentinel Monitoring: We track the system 24/7 for latency, token usage, and drift.
-
Value Reporting: You receive a dashboard showing the immediate impact: Hours Saved, Error Rate Reduction, and ROI realized.